What is SOC as a Service (SOCaaS)?
SOC-as-a-Service (SOCaaS) is a subscription-based security approach where a third-party manages a SOC via the cloud.
SOCaaS delivers all standard in-house SOC services like network monitoring, log management, threat detection, incident response, reporting, and compliance. The service provider also manages necessary personnel, processes, and technology, offering 24/7 support.
What is SOC?
A Security Operations Center (SOC) is a company’s intelligence hub, aggregating real-time data from various digital assets to identify and respond to cybersecurity threats using intelligent automation. For further details on SOC, see our related post:
Why is SOC as a Service (SOCaaS) Important?
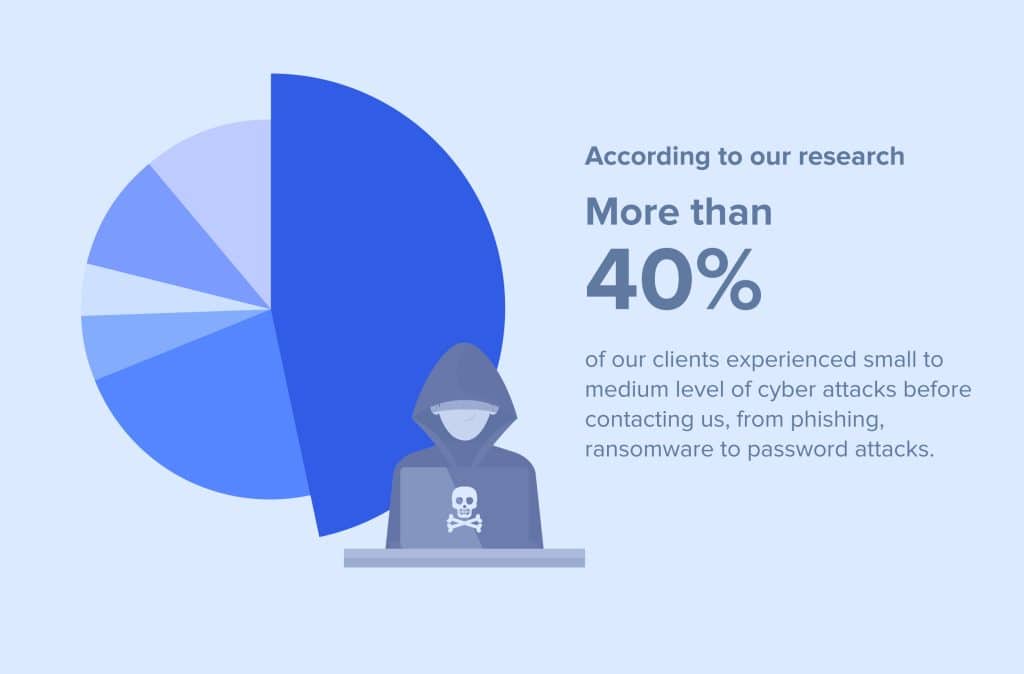
The shift to digital transformation and cloud services has significantly expanded most organizations’ vulnerability to cyber attacks. As workforces become more remote, cyber attackers exploit these changes, a trend amplified by the Covid pandemic. According to our reseach, over 40% of our clients experienced small to medium level of cyber attacks before contacting us, from phishing, ransomware to password attacks.
To secure sensitive data and comply with data protection regulations, many of our clients invested heavily in advanced on-site and cloud security monitoring tools. Although these tools were effective in identifying potential threats, they generated an overwhelming number of daily security alerts. With a small in-house IT team, managing these alerts became an uphill task.
Recognizing the need for a more efficient way to handle the security alerts, Many SMEs or large corporates like our clients turned to SOC-as-a-Service (SOCaaS). The shift to SOCaaS was driven by the following factors:
Handling Security Alert Overload
Many SMEs small IT team was struggling to manage the flood of daily security alerts. The SOCaaS provider offered 24/7 monitoring and intelligent alert prioritization, ensuring that real threats were identified and addressed swiftly.
Maximizing Existing Security Investments
The SOCaaS solution enabled corporates to get more value from their existing security investments, as the SOCaaS provider’s expertise helped optimize the use of their current security tools.
Expanding Security Monitoring
With SOCaaS, companies are able to extend security monitoring to include their cloud services, operational technology (OT), and IoT devices, an area they’d struggled with previously.
Improving Security Investments’ Effectiveness
SOCaaS providers offer continuous monitoring and periodic assessments, enabling SMEs and corporates alike to measure and improve the effectiveness of their current security investments.
Demonstrating a Concerted Security Effort
SOCaaS also provide companies with a way to show auditors and stakeholders a comprehensive and standardized threat detection and response capability, bolstering their credibility in managing cybersecurity risks.
How does SOCaaS integrate into the security architecture?
SOCaaS, as a managed service, can be provided by an external vendor as an independent offering. However, it’s commonly included as a component of a comprehensive security bundle and should be harmonized with other security instruments and services within the company’s security framework.
The Differences Between SIEM and SOC
Despite their symbiotic relationship, SIEM and SOC are distinct entities within an organization’s cybersecurity framework. A SIEM solution is focused on collecting, correlating, and analyzing data from various sources to identify potential threats. Conversely, a SOC utilizes this data, among other information, to monitor and respond to security incidents.
While a SIEM is a tool or a set of tools, a SOC is a team. The SIEM provides the SOC with the crucial data and analyses needed to make informed decisions about the security posture of an organization.
For further reading, please visit our blog!
Benefits of SOC as a Service (SOCaaS)
1. Quicker Detection and Response
SOCaaS providers offer dedicated analysts to quickly detect and resolve cyber threats, reducing the multitasking burden on in-house teams.
2. Specialized Security Expertise
SOCaaS vendors provide access to specialized analysts for various needs, such as endpoint containment, threat hunting, and malware analysis, which can be beneficial when seeking a reliable vendor.
3. Improved Security Maturity
SOCaaS can rapidly enhance a customer’s security program. If in-house talent acquisition is lacking, finding the right SOCaaS partner might be a more efficient strategy.
4. Cost Savings
Building an in-house SOC can be expensive and includes start-up costs and potential staff turnover (According to Tines survey, 71% of analysts suffer burnout). On the other hand, SOCaaS is generally a more cost-effective solution, offering managed services that help prevent job burnout among security analysts.

SOC as a Service Job Duties
SOC-as-a-Service (SOCaaS) responsibilities encompass a variety of roles aimed at providing round-the-clock security monitoring and threat management. Here are some of the key roles and responsibilities involved:
Security Analyst Tier 1 – Triage
These professionals categorizes and prioritizes alerts, and escalates incidents to tier 2 analysts.
Security Analyst Tier 2 – Incident Responders
Their main role is to manage and respond to security incidents. They are responsible for identifying the severity of incidents, coordinating responses, and ensuring that breaches are contained and remediated.
Security Analyst Tier 3 – Forensic Experts
In the event of a breach, forensic experts investigate the incident. They identify how the breach occurred, what data was compromised, and provide recommendations for preventing similar incidents in the future.
Compliance Officers
They ensure that the organization is in compliance with various security standards and regulations. They conduct regular audits, identify areas of non-compliance, and provide guidance on how to achieve and maintain compliance.
Security Engineers
These professionals are responsible for managing and maintaining the security infrastructure. They oversee the implementation of security tools and technologies, manage updates and patches, and troubleshoot any technical issues.
Security Managers or SOC Managers
They oversee the entire security operation. They are responsible for strategic planning, managing the security team, liaising with other business units, and reporting to senior management or the board.
SOC as a Service Challenges
Transition Phase
Engaging a SOCaaS provider involves a sensitive transition period where the provider adjusts its technology to the client’s environment, and the client prepares its network for the provider’s monitoring protocols.
Data Security
Data security on the provider’s side is crucial. Clients should choose a provider with strong defenses to protect their enterprise data, much like considering a supply chain issue.
Log Delivery Costs
Full access to a provider’s operations related to a specific client can be costly. Even though the data comes from the client’s network, the actions belong to the SOCaaS provider, making full log data access expensive.
Regulatory Compliance
Compliance with regulatory standards is key when outsourcing security operations. Consistent reporting is vital for maintaining compliance, and it’s important to know whether the SOCaaS provider handles compliance or outsources it.
SOC Inhouse Vs SOC as a Service
When choosing between an in-house Security Operations Center (SOC) and SOC-as-a-Service (SOCaaS), businesses should consider factors such as cost, expertise, scalability, and focus. Here’s a comparison of both:
In-house SOC:
- Expertise: An in-house team can have a deep understanding of the company’s systems and business environment. However, maintaining a diverse range of expertise can be challenging due to the broad scope of security threats.
- Cost: Building and maintaining an in-house SOC can be expensive. Costs include not just technology, but also recruitment, training, and retention of skilled security professionals.
- Scalability: Scaling an in-house SOC can be difficult and costly, especially for small and medium-sized businesses.
- Focus: An in-house SOC allows companies to focus on threats specific to their industry or business. However, managing a SOC may distract from the company’s core business.
SOCaaS:
- Expertise: SOCaaS providers specialize in security and have a broad range of expertise. They stay updated on the latest threats and security technologies.
- Cost: SOCaaS can be more cost-effective, as it spreads the cost of technology and expertise across multiple clients. It also eliminates the costs related to hiring and training personnel.
- Scalability: SOCaaS can easily scale with the business, accommodating changes in size and complexity without major additional investments.
- Focus: With SOCaaS, companies can focus on their core business while the service provider focuses on security.
In summary, while an in-house SOC can offer deep knowledge of the company’s specific context, SOCaaS provides a more cost-effective, scalable, and focused solution. The choice will depend on the company’s specific needs, resources, and risk profile.
Final Thoughts
In conclusion, SOCaaS is a valuable option for many businesses, offering an outsourced, scalable, and cost-effective solution for cybersecurity. However, as with any important business decision, it’s essential for each organization to carefully evaluate its unique needs, resources, and risk profile before choosing to adopt SOCaaS.
THREE IC: Your SOCaas Provider
In a world where cyber threats are constantly evolving, it’s imperative to have a reliable partner in your corner. With THREE IC, you’re not just getting a service provider but a dedicated partner committed to safeguarding your digital assets. Our comprehensive SOCaas services can significantly bolster your defense strategy.
Additionally, our range of IT support services is designed to cover all your IT needs, providing you with a seamless and worry-free digital experience. So why wait? Get in touch with a trusted IT consultant at THREE IC today. Because when it comes to protecting what’s valuable, you deserve nothing but the best. Secure your digital assets now, for peace of mind tomorrow.